|
|
原文在 => Single Packet Authorization with Fwknop by Michael Rash December, 2005.
一年多以前, 我看到 朝陽 洪朝貴 老師 寫了這篇文章 "連鑰匙孔都藏起來的 ssh 完全防禦: SPA" ... 當時, 我沒有實測, 不了解整個運作起來是怎樣的情形 ... 我認為有 Fail2Ban 就足夠了 ...
有灌過 SSH Server 的人, 如果查看伺服器的日誌(例如 : /var/log/auth.log ) , 可能多多少少會發現每天有些許外面的程式, 以 "root" ID, 或"某某某" User ID 來嘗試看看能否登入到你的 SSH Server ... 我的伺服器即便有灌 Fail2Ban 也是躲不過 ... 於是, 我從允許 ""root" 帶密碼" 登入 SSH Server, 改成 "PermitRootLogin no" ... 過一段日子, 覺得還是不太放心, 再改成 ... :
- PermitRootLogin no
- PubkeyAuthentication yes
- AuthorizedKeysFile .ssh/authorized_keys .ssh/authorized_keys2
- PasswordAuthentication no
- ...
幾個星期前, 我再次觀看 "連鑰匙孔都藏起來的 ssh 完全防禦: SPA", 並且實測 ... 我想, 如果連"孔洞"都消失的話, 那麼, 要登入伺服器, 可能得另謀其他管道 ... 所以, 我就來學學該怎麼樣能讓鑰匙孔消失和適時的出現 ...
經過幾番周折, 終於學會使用這項技巧 ... 
現我在伺服器(ip : 45.77.17.138) 這邊安裝了 SSH Server 以及 Fwknop Server ...
提供 Tcp Port 7, 用於 echo 測試 ...
/etc/fwknop/fwknopd.conf :
- PCAP_INTF ens3;
- PCAP_FILTER udp port 62201;
/etc/fwknop/access.conf :
- REQUIRE_SOURCE_ADDRESS N
- SOURCE ANY
- OPEN_PORTS tcp/22
- KEY_BASE64 保密不公開
- HMAC_KEY_BASE64 保密不公開
- SOURCE ANY
- OPEN_PORTS tcp/7
- KEY_BASE64 e4HchGSfm4DdfpI8LQsUPe/dVVeI0xZBDq6cpC8arO8=
- HMAC_KEY_BASE64 MK4MKf/em/E/ZtZ3cRFn5wFEM0NKCtODBhjzt9FOnmJOVEis3gluhKPlSCobtH9r/UnpqsD7vLN8kXueKcmvyA==
伺服器的防火牆設定 ... :
- root@vultr:~# iptables -L
- Chain INPUT (policy ACCEPT)
- target prot opt source destination
- FWKNOP_INPUT all -- anywhere anywhere
- f2b-sshd tcp -- anywhere anywhere multiport dports ssh
- ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate RELATED,ESTABLISHED
- DROP tcp -- anywhere anywhere tcp dpt:ssh
- DROP tcp -- anywhere anywhere tcp dpt:echo
- Chain FORWARD (policy ACCEPT)
- target prot opt source destination
- Chain OUTPUT (policy ACCEPT)
- target prot opt source destination
- Chain f2b-sshd (1 references)
- target prot opt source destination
- RETURN all -- anywhere anywhere
- Chain FWKNOP_INPUT (1 references)
- target prot opt source destination
Client 端, /root/.fwknoprc :
- [default]
- WGET_CMD /usr/bin/wget
- [my.server.com_tcp22]
- ACCESS tcp/22
- KEY_BASE64 保密不公開
- HMAC_KEY_BASE64 保密不公開
- SPA_SERVER 45.77.17.138
- USE_HMAC Y
- [my.server.com_tcp7]
- ACCESS tcp/7
- KEY_BASE64 e4HchGSfm4DdfpI8LQsUPe/dVVeI0xZBDq6cpC8arO8=
- HMAC_KEY_BASE64 MK4MKf/em/E/ZtZ3cRFn5wFEM0NKCtODBhjzt9FOnmJOVEis3gluhKPlSCobtH9r/UnpqsD7vLN8kXueKcmvyA==
- SPA_SERVER 45.77.17.138
- USE_HMAC Y
底下顯示了這台伺服器, 大概有三個 Tcp Port 可能被過濾掉了 ... :
- root@debian:~# nmap -A -v 45.77.17.138
- Starting Nmap 7.70 ( https://nmap.org ) at 2020-09-21 17:45 CST
- NSE: Loaded 148 scripts for scanning.
- NSE: Script Pre-scanning.
- Initiating NSE at 17:45
- Completed NSE at 17:45, 0.00s elapsed
- Initiating NSE at 17:45
- Completed NSE at 17:45, 0.00s elapsed
- Initiating Ping Scan at 17:45
- Scanning 45.77.17.138 [4 ports]
- Completed Ping Scan at 17:45, 0.20s elapsed (1 total hosts)
- Initiating Parallel DNS resolution of 1 host. at 17:45
- Completed Parallel DNS resolution of 1 host. at 17:45, 0.00s elapsed
- Initiating SYN Stealth Scan at 17:45
- Scanning 45.77.17.138.vultr.com (45.77.17.138) [1000 ports]
- Increasing send delay for 45.77.17.138 from 0 to 5 due to 37 out of 121 dropped probes since last increase.
- Increasing send delay for 45.77.17.138 from 5 to 10 due to max_successful_tryno increase to 4
- Increasing send delay for 45.77.17.138 from 10 to 20 due to 11 out of 31 dropped probes since last increase.
- Increasing send delay for 45.77.17.138 from 20 to 40 due to max_successful_tryno increase to 5
- Increasing send delay for 45.77.17.138 from 40 to 80 due to 11 out of 22 dropped probes since last increase.
- Increasing send delay for 45.77.17.138 from 80 to 160 due to 11 out of 27 dropped probes since last increase.
- Increasing send delay for 45.77.17.138 from 160 to 320 due to 11 out of 27 dropped probes since last increase.
- SYN Stealth Scan Timing: About 31.16% done; ETC: 17:47 (0:01:08 remaining)
- SYN Stealth Scan Timing: About 40.54% done; ETC: 17:48 (0:01:29 remaining)
- SYN Stealth Scan Timing: About 66.96% done; ETC: 17:49 (0:01:13 remaining)
- SYN Stealth Scan Timing: About 76.34% done; ETC: 17:49 (0:00:55 remaining)
- SYN Stealth Scan Timing: About 85.74% done; ETC: 17:49 (0:00:35 remaining)
- Completed SYN Stealth Scan at 17:50, 263.77s elapsed (1000 total ports)
- Initiating Service scan at 17:50
- Initiating OS detection (try #1) against 45.77.17.138.vultr.com (45.77.17.138)
- adjust_timeouts2: packet supposedly had rtt of -189579 microseconds. Ignoring time.
- adjust_timeouts2: packet supposedly had rtt of -189579 microseconds. Ignoring time.
- Retrying OS detection (try #2) against 45.77.17.138.vultr.com (45.77.17.138)
- Initiating Traceroute at 17:50
- Completed Traceroute at 17:50, 3.02s elapsed
- Initiating Parallel DNS resolution of 10 hosts. at 17:50
- Completed Parallel DNS resolution of 10 hosts. at 17:50, 0.05s elapsed
- NSE: Script scanning 45.77.17.138.
- Initiating NSE at 17:50
- Completed NSE at 17:50, 0.01s elapsed
- Initiating NSE at 17:50
- Completed NSE at 17:50, 0.00s elapsed
- Nmap scan report for 45.77.17.138.vultr.com (45.77.17.138)
- Host is up (0.063s latency).
- Not shown: 997 closed ports
- PORT STATE SERVICE VERSION
- 7/tcp filtered echo
- 22/tcp filtered ssh
- 139/tcp filtered netbios-ssn
- Too many fingerprints match this host to give specific OS details
- Network Distance: 15 hops
- TRACEROUTE (using port 8888/tcp)
- HOP RTT ADDRESS
- 1 1.56 ms I-040GW.cht.com.tw (192.168.1.1)
- 2 2.61 ms tp240-143.dialup.seed.net.tw (139.175.240.143)
- 3 2.18 ms 192.72.223.9
- 4 8.46 ms r58-205.seed.net.tw (139.175.58.205)
- 5 8.96 ms r58-145.seed.net.tw (139.175.58.145)
- 6 9.95 ms h202-192-72-155.seed.net.tw (192.72.155.202)
- 7 9.94 ms h202-192-72-155.seed.net.tw (192.72.155.202)
- 8 9.95 ms 199.245.16.37
- 9 38.43 ms ae-7.r31.tokyjp05.jp.bb.gin.ntt.net (129.250.7.5)
- 10 65.63 ms ce-0-14-0-1.r02.tokyjp05.jp.ce.gin.ntt.net (120.88.54.98)
- 11 ... 14
- 15 62.59 ms 45.77.17.138.vultr.com (45.77.17.138)
- NSE: Script Post-scanning.
- Initiating NSE at 17:50
- Completed NSE at 17:50, 0.00s elapsed
- Initiating NSE at 17:50
- Completed NSE at 17:50, 0.00s elapsed
- Read data files from: /usr/bin/../share/nmap
- OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
- Nmap done: 1 IP address (1 host up) scanned in 271.50 seconds
- Raw packets sent: 1329 (62.326KB) | Rcvd: 1284 (55.408KB)
送 "Hello" 字眼過去至伺服器, 但沒能收到 echo ... :
- root@debian:~# echo "Hello" | nc 45.77.17.138 7
- (UNKNOWN) [45.77.17.138] 7 (echo) : Connection timed out
送 "密語" 至伺服器, 請它暫時(30秒)打開 Tcp Port 7 的通道 ... 我並緊接著送 "Hello" 字眼過去, 隨後即收到正確的 echo ... :
- root@debian:~# fwknop -n my.server.com_tcp7 --verbose -R
- [+] Resolved external IP (via '/usr/bin/wget -U Fwknop/2.6.10 --secure-protocol=auto --quiet -O - https://www.cipherdyne.org/cgi-bin/myip') as: 112.105.240.229
- SPA Field Values:
- =================
- Random Value: 4646262537257489
- Username: root
- Timestamp: 1600683550
- FKO Version: 3.0.0
- Message Type: 1 (Access msg)
- Message String: 112.105.240.229,tcp/7
- Nat Access: <NULL>
- Server Auth: <NULL>
- Client Timeout: 0
- Digest Type: 3 (SHA256)
- HMAC Type: 3 (SHA256)
- Encryption Type: 1 (Rijndael)
- Encryption Mode: 2 (CBC)
- Encoded Data: 4646262537257489:cm9vdA:1600683550:3.0.0:1:MTEyLjEwNS4yNDAuMjI5LHRjcC83
- SPA Data Digest: YGFMxQ+C2a4HojasVflYqm05eRC0DWaNrmM6ewF7Ukw
- HMAC: dGpdcQ3rXvKbxFIWBCDdCVmaSU+QNL31fHDYtEBstUg
- Final SPA Data: 8hcLdcIPNfRHY1t1KHrFh6vLxUAlXG4kS287gTMhYdzc7g+lL0X0kCbc4WvB65ZwVrmHp78s0mNVVM7jtMUwcgLF1Vb7jqBpEL/YF9wvk6R5V/V+CJK6pGeKJgf8nnfI8GOOztsRufKl3W47qsBWJxt2Iu0jyNz7rhNa/UcmWCZMjIH4MI+KAXdGpdcQ3rXvKbxFIWBCDdCVmaSU+QNL31fHDYtEBstUg
- Generating SPA packet:
- protocol: udp
- source port: <OS assigned>
- destination port: 62201
- IP/host: 45.77.17.138
- send_spa_packet: bytes sent: 225
- root@debian:~#
- root@debian:~# echo "Hello" | nc 45.77.17.138 7
- Hello
- ^C
使用 Windows 版的 fwknop-gui.exe 來送 "密語" 至伺服器, 請它暫時(30秒)打開 Tcp Port 7 的通道 ... :
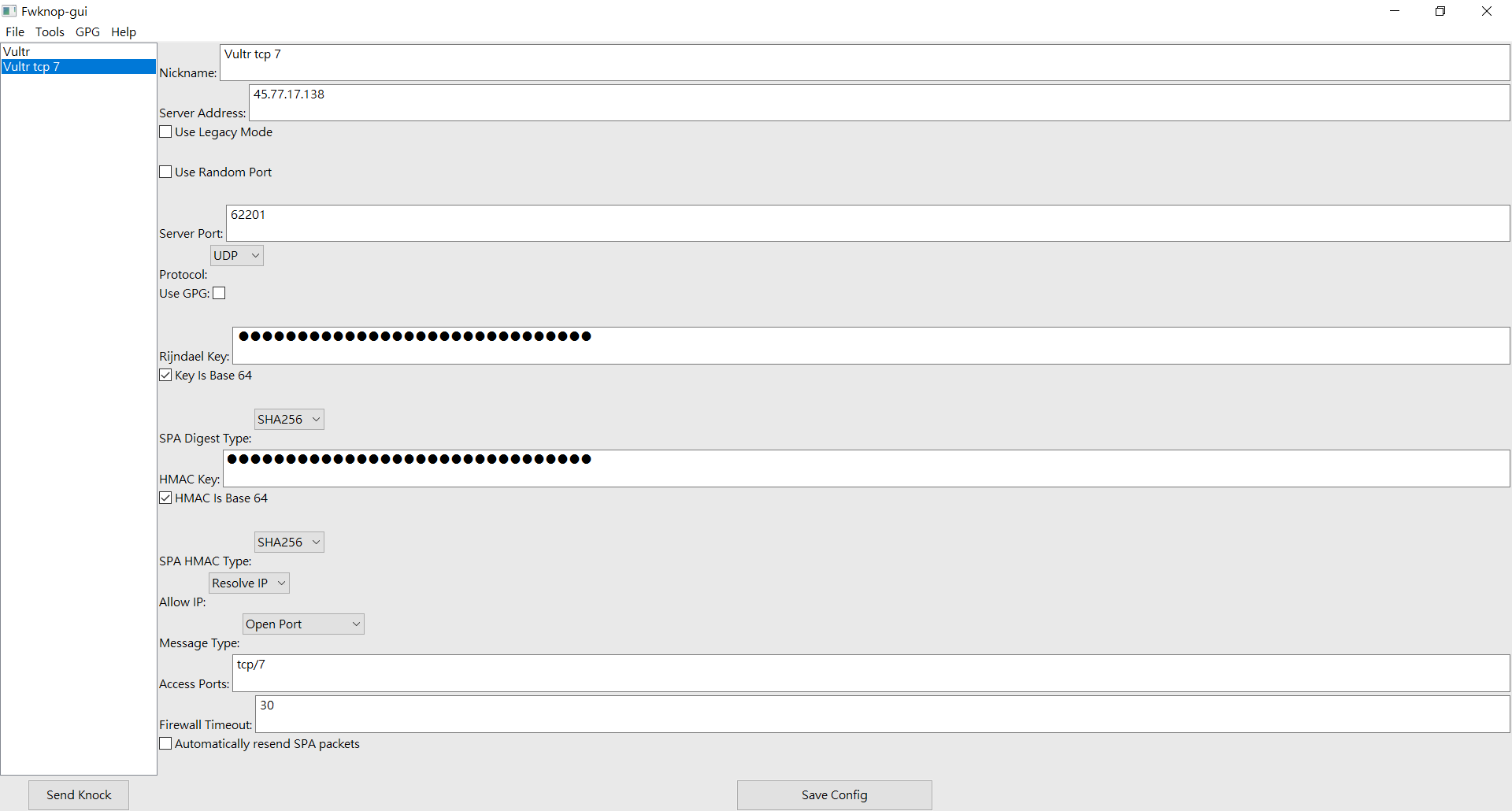
在 Fwknop-gui 的 "Rijndael Key" 欄, 應填入與伺服器同樣的 KEY_BASE64 值, 這台伺服器(ip : 45.77.17.138) 的 KEY_BASE64 值如下 :
- e4HchGSfm4DdfpI8LQsUPe/dVVeI0xZBDq6cpC8arO8=
在 Fwknop-gui 的 "HMAC Key" 欄, 應填入與伺服器同樣的 HMAC_KEY_BASE64 值, 這台伺服器(ip : 45.77.17.138) 的 HMAC_KEY_BASE64 值如下 :
- MK4MKf/em/E/ZtZ3cRFn5wFEM0NKCtODBhjzt9FOnmJOVEis3gluhKPlSCobtH9r/UnpqsD7vLN8kXueKcmvyA==
Windows 版 fwknop-gui by jp-bennett
倒數 30 秒 ... :
再緊接著送 "Hello" 字眼過去, 隨後即收到正確的 echo ... :
- D:\Download-Files\Netcat\netcat-master\netcat-master>echo "Hello" | nc.exe 45.77.17.138 7
- "Hello"
- ^C
Windows 環境下可用的 Netcat(即 nc ) by diegocr
產生自己要用的相關鍵值, 但不存檔 ... :
- root@vultr:~# fwknop -A tcp/7 -D my.server.com --key-gen --use-hmac
- [*] Creating initial rc file: /root/.fwknoprc.
- KEY_BASE64: 4EDJvs0WnM69iWi2Z89LdTcmanyE2zBQK5qJNjjkakg=
- HMAC_KEY_BASE64: Xjp80RpD9hSrYCnBPKgwNFtOINH8C9wVNAny4v+aWyATGOoHuY6MDhladFhgOeoRpFp7T9/o/sprxqb6N+Y2vw==
產生自己要用的相關鍵值, 並且存檔記錄下來 ... :
- root@vultr:~# fwknop -A tcp/22 -D my.server.com --key-gen --use-hmac --save-rc-stanza
- [+] Wrote Rijndael and HMAC keys to rc file: /root/.fwknoprc
- root@vultr:~# ls -la
- total 80
- drwx------ 4 root root 4096 Sep 21 11:57 .
- drwxr-xr-x 18 root root 4096 Sep 5 06:43 ..
- -rw------- 1 root root 10467 Sep 20 06:43 .bash_history
- -rw-r--r-- 1 root root 564 Sep 5 00:41 .bashrc
- -rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc.first
- -rw------- 1 root root 43 Sep 20 22:12 .fwknop.run
- -rw------- 1 root root 324 Sep 21 11:57 .fwknoprc
- -rw------- 1 root root 513 Sep 20 22:06 .fwknoprc.Good
- drwx------ 3 root root 4096 Sep 11 20:09 .gnupg
- -rw------- 1 root root 92 Sep 20 19:00 .lesshst
- -rw-r--r-- 1 root root 148 Aug 17 2015 .profile
- drwx------ 2 root root 4096 Sep 5 15:09 .ssh
- -rw------- 1 root root 11609 Sep 20 23:23 .viminfo
- -rw-r--r-- 1 root root 10240 Sep 12 18:29 iptables.20200913-0230.tar
- root@vultr:~# cat .fwknoprc
- [default]
- [my.server.com]
- ACCESS tcp/22
- SPA_SERVER my.server.com
- KEY_BASE64 3AVKPD/09DNHwxKSvZ0eH9GxOwMGbp4apbzayPU2C3U=
- HMAC_KEY_BASE64 yGlj/yT1OepkrE6dGCdpzuqwJAe+7h26K/y487cMrOxGmhfVBw1n/v+vuKpg3NffxiIaqASCPRZ0zMbPyS1gzw==
- USE_HMAC Y
沒有送打開孔洞的通關密語, 所以, 連接 Tcp Port 22 失敗 ... :
- root@debian:~# ssh 45.77.17.138
- ssh: connect to host 45.77.17.138 port 22: Connection timed out
送了打開孔洞的通關密語過去, 可以正常連接到 Tcp Port 22 ... :
- root@debian:~# fwknop -n my.server.com_tcp22 --verbose -R
- [+] Resolved external IP (via '/usr/bin/wget -U Fwknop/2.6.10 --secure-protocol=auto --quiet -O - https://www.cipherdyne.org/cgi-bin/myip') as: 112.105.240.229
- SPA Field Values:
- =================
- Random Value: 4699983468226520
- Username: root
- Timestamp: 1600691688
- FKO Version: 3.0.0
- Message Type: 1 (Access msg)
- Message String: 112.105.240.229,tcp/22
- Nat Access: <NULL>
- Server Auth: <NULL>
- Client Timeout: 0
- Digest Type: 3 (SHA256)
- HMAC Type: 3 (SHA256)
- Encryption Type: 1 (Rijndael)
- Encryption Mode: 2 (CBC)
- Encoded Data: 4699983468226520:cm9vdA:1600691688:3.0.0:1:MTEyLjEwNS4yNDAuMjI5LHRjcC8yMg
- SPA Data Digest: fMAweWrcz3BrxIQ7gz2Kxfq1RthpwWJgrDJco60m3sI
- HMAC: 2uVqLu2+dHq7w7zIGueebYmrLq5nu7pUiwaZyW6MFck
- Final SPA Data: /7VtsmqmKFl6Nf1e3QuyjFucoWJF88419LlSOfnRXKHauKNVDkpHqBSCV4gEAYoqrpo6i9M38j5S9KqEdYqHjTsDotMIwUWPKOmPYAtBmhneH3+CfmkrlLCJmXma9MnUfCNF3jrZdGN89zZw+qYAmlm9+5INTIro49iyKfa8wWPabLWSTnr1Ld2uVqLu2+dHq7w7zIGueebYmrLq5nu7pUiwaZyW6MFck
- Generating SPA packet:
- protocol: udp
- source port: <OS assigned>
- destination port: 62201
- IP/host: 45.77.17.138
- send_spa_packet: bytes sent: 225
- root@debian:~# ssh 45.77.17.138
- The authenticity of host '45.77.17.138 (45.77.17.138)' can't be established.
- ECDSA key fingerprint is SHA256:8wtDpO6DT2WzDO5wdU9pHBJU3iOELf0Q/EXfnoZioJ8.
- Are you sure you want to continue connecting (yes/no)? yes
- Warning: Permanently added '45.77.17.138' (ECDSA) to the list of known hosts.
- root@45.77.17.138's password:
在這裡, 因為我沒有公佈伺服器(ip : 45.77.17.138) 現在 Tcp Port 22 所使用的相關鍵值, 所以, 請有興趣要測試 Fwknop Server 的人, 使用 Tcp Port 7, 及其相關鍵值來測試...
相關參考網頁, 參註二.
註一.
Understanding the SSH Encryption and Connection Process
設定密不透水的 ssh 服務
定期排程異地備份不需要密碼, 就交給 ssh 的信任機制與身份識別吧!
關閉sshd的登入密碼認證(PasswordAuthentication)
註二.Fwknop, Debian and Ansible
Single Packet Authorization with GnuPG Keys
利用fwknop給sshd加一道門,向暴力黑客Say no-way!
|
|